These days, with bandwidth rising substantially, most businesses have to have a robust and secure wireless connection to support all the devices that are in need of connection. This opens up a lot of questions on how best to go about doing this. Today, we will discuss some of the very best practices you should consider when you are putting together your business’ Wi-Fi network.
BNMC Blog
Most modern businesses depend on wireless Internet connectivity (Wi-Fi) to a certain extent. Do you know what it means when we talk about the various speeds of routers, the data they can transfer, and so on? Today, we wanted to clear up some facts about dual-band routers that your business might find handy in the future.
Most of us all work on laptops or desktops everyday. It’s pretty easy to assume that cybersecurity generally stops there. You’ve got your secure passwords, your antivirus, and that little icon on the bottom right telling you that you are secure—you should be good to go then, right?
Unfortunately, it’s more complex than that.
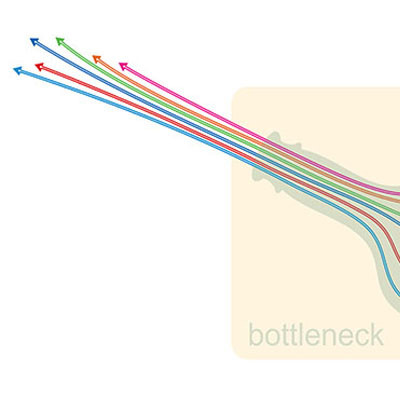
Sometimes your network will get bogged down for apparently no reason. Well, we hate to break it to you, but there is almost sure to be a reason, one of which could be a network bottleneck. A network bottleneck could very well harm your network to the point where productivity and efficiency are impacted. How do you discover a bottleneck and resolve it?
Not long ago, connectivity required an actual, physical connection between two endpoints. As a result, a wired connection was the only option for businesses to access online materials and resources. Today, businesses have a choice to make: is a wired connection better for my operations, or should I implement wireless connectivity?
Many businesses rely on the concept of a shared network, where all computers have access to centralized folders and drives so documents can be accessed by everyone. While it is likely that your IT department has already taken care of the nitty-gritty details of this, we thought it might be helpful to put together a short guide on how you can map a network on your personal device on the off-chance you want to set up a shared network for your own personal reasons.
Nearly everyone uses Wi-Fi. Wireless gives people the increased flexibility to use their mobile devices in more places. If your business’ Wi-Fi isn’t set up properly, you’ll find that your coverage will be lacking. Today, we thought we’d give you a few tips on how to set up your Wi-Fi connection so that it works best for your business.
Regardless of how long they stay in a medical facility, patients and their visitors now expect that they will have access to wireless Internet during their time there. While it was once just a convenience, it is now an essential part of ensuring that they remain comfortable. As such, it is now the responsibility of the healthcare facility to ensure that their Wi-Fi is fast, reliable, and accessible.
As businesses have come to rely on increasing amounts of data, the importance of keeping this data organized and usable has also increased. Therefore, databases are a critical consideration for any business that wants to gain as much value as they can from their collected data. However, a database can only be useful if a database management system is involved. Let’s go into why this is.
While it is only too easy to reduce the benefits of Voice over Internet Protocol (VoIP) solutions to “It’s cheaper than the other way!”, there are many more benefits that a small business could find quite advantageous. Today, we’ll go over a few of these other benefits – but as we do, keep in mind that the “cheaper” part still applies.
Certain useful business technologies, like VoIP, screen-sharing, and webinar platforms, require a lot out of your Internet connection. This means that you need to be sure that you have sufficient bandwidth to support these solutions. Today, we’re taking a look at how your business relies on having the appropriate bandwidth to support your operations, and how to find out if it does.
Implementing technology solutions for your organization always comes with a risk, and if your business is blindsided by it, risk can derail productivity and get in the way of success. As a business owner, understanding this risk and planning for it is critical to your organization’s continued success. This week’s tip is dedicated to helping you identify risk and the role it should play in your decision making.
Your choice of browser can easily impact your security, as each handles how it informs you whether or not your connection is encrypted differently. This is especially important to recognize, especially when the Chrome browser will soon run counter to the advice users have received for quite some time.
Network is a word that’s commonly seen in the office environment in many different ways. In particular, you’re likely to hear about network security, network maintenance, social networking, and network switches, but what does it all mean? In this week’s tech term, we’re going to address what a network is and how it works to tie your business together.
A network is arguably one of the most important assets that your business has. It keeps your team connected to crucial information and mission-critical applications. This is perhaps why it’s so irritating when your network acts up. You should be on the lookout for even the slightest problem with your network, as even a small change could be a sign of bad things yet to come.
 Security is a top priority in today’s business environment, especially following high-profile hacks of notable enterprises. Unfortunately, the fact of the matter is that these hacks could have been prevented if both the employees and employers of these organizations followed strict security best practices for their technology. Thankfully, it doesn’t have to be hard to teach your team how to properly use technology.
Security is a top priority in today’s business environment, especially following high-profile hacks of notable enterprises. Unfortunately, the fact of the matter is that these hacks could have been prevented if both the employees and employers of these organizations followed strict security best practices for their technology. Thankfully, it doesn’t have to be hard to teach your team how to properly use technology.