BNMC Blog
Tip of the Week: How to Make Your Credentials More Memorable
Let’s face facts: as critical to your security as they are, passwords are kind of the worst. Of course, since they are so critical, you need to make sure all of the ones you use are as secure as possible, so we’ve assembled some practices that may help you tip the scales in your favor. Spoiler alert: the conventional password may not be your first choice for much longer.
What Not to Do
There’s a tricky balance to strike when devising a password. On the one hand, you want it to be sufficiently secure, but on the other, you don’t want to make it too difficult to get back in for yourself, either.
This is probably the reason that so many password rules and best practices are broken and ignored: user convenience.
Let’s take a look at the top 15 results of some data compiled by the United Kingdom’s National Cyber Security Centre with the help of the security website Have I Been Pwned, regarding the most commonly breached passwords:
- 123456
- 123456789
- qwerty
- password
- 1111111
- 12345678
- abc123
- 1234567
- Password1
- 12345
- 1234567890
- 123123
- 000000
- Iloveyou
- 1234
Just glancing over this list, you can very easily see how a few of the simplest password quality rules are broken - common words, common number strands, and hardly any mix of alphanumeric characters.
It is probably also a safe bet that a person who would use a password like this would also be the person to repeat their password across accounts. This means that if one of their accounts were breached, they all would be rendered insecure.
Of course, now that we’ve clearly outlined the problem, we have a proposed strategy to help fix it.
Using a Truly Random Passphrase
One way that you can improve upon password security is known as the passphrase. Instead of using random characters, random words are used, helping to make it both more complicated and easier to remember.
The web comic xkcd does a good job of explaining it:
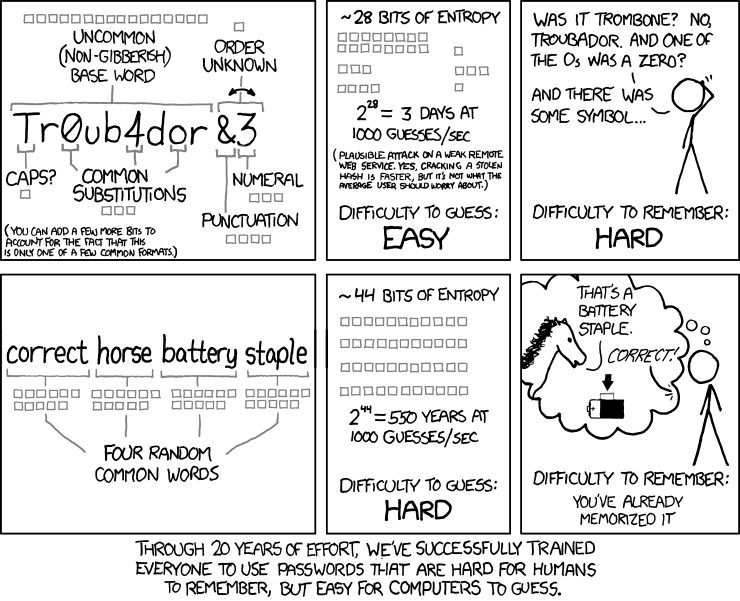
However, this opens us up to new issues - like the very human instinct to stick to a pattern of some sort. Good for survival, not so great when you’re looking for true randomness.
This is why an IT professional named Arnold Reinhold developed a new method of generating a passphrase, called Diceware.
Taking a die, roll it five times, taking note of the numbers you’ve rolled. Whatever the 5-digit number you produced was, find it on the official Diceware word list. That is now the first word of your passphrase. Repeat this process until you have six or seven words in your passphrase. This helps eliminate human bias from the selection process, making this process about as random as possible.
Demonstrating Diceware in Action
Rolling a die, I came up with 45656. Diceware says that’s “pleat.”
My next roll came up 13211. “Bach.”
34663, making the next word “Julie.”
32135 means the next word is “gulp.”
32565, for a final word “choice” of “Hera.”
So, my new passphrase is “pleatBachJuliegulpHera.” Gibberish, yet still far more memorable than the alternative system.
Remembering All These Passphrases
So, with the “random” part of our concerns addressed, there is still the concern that remembering so many different passphrases may be a bit much to ask. This is why we recommend that you combine your use of passphrases with the use of a password manager.
These handy programs secure all of your passwords (or passphrases) in a secure vault, ready for you to access with a single, master password (or passphrase). As a result, as long as you can remember one passphrase, you can use the password manager to handle the rest of your accounts.
For help in implementing all of this (or with any other assistance with your business’ information technology) give BNMC a call at (978) 482-2020. What other tips would you like us to cover? Let us know in the comments, and subscribe so you don’t miss it!



Comments